Sep 26, 2024
Tor Darknet

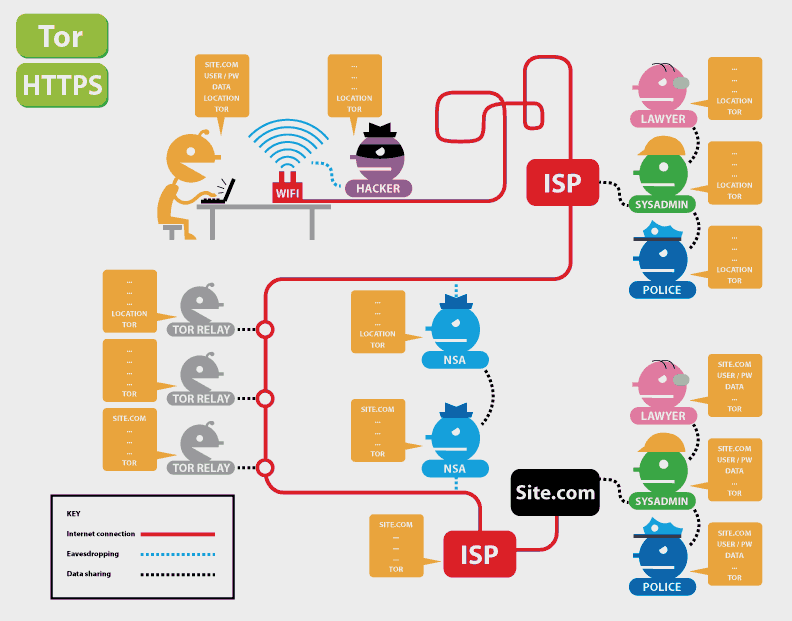
Tor is an anonymous internet proxy that directs traffic through a worldwide volunteer network of thousands of relays. Tor wraps messages in. Steps to AccessDark Web using Tor Browser in Kali Linux. Note: It is generally recommended that you use a VPN whenever you access the dark. Is it illegal to buy an iPhone off the dark web? No it cant be. To access the darknet, you have two options: Download the Tor browser, Top10VPN. Dark Web Typosquatting: Scammers v. Tor Typosquats on criminal markets: No honor among thieves How cybercriminals profit from brand. With an encrypted and anonymous connection, Tor helps you access the unindexed part of the internet known as the dark web. Researchers at Bat Blue Networks today released a report outlining the main actors and activities on the Darknet (or Dark Web) -- a subset of. Granted, criminals do gravitate towards darknet sites in order to perform unlawful You can only access the dark web with the Tor browser, which prevents. Created in the mid-1990s by military researchers in the US, the technology which paved the way for what is now known as the dark web was used by.
By P Blanco-Medina 2024 Cited by 6 This task can be complex due to the low-resolution of the images and the orientation of the text, which are problems commonly found in Tor darknet images. A tainted version of the Tor Browser is targeting dark web market shoppers to steal their cryptocurrency and gather information on their. With an encrypted and anonymous connection, Tor helps you access the unindexed part of the internet known as the dark web. Defend yourself against tracking and surveillance. Circumvent censorship. Download. Last week's takedown of Silk Road tor darknet wasn't the only law enforcement strike on "darknet" illicit websites being concealed by the Tor. How to Access the Deep Web Using Tor Composition of the Deep Web. 54 Publicly available databases. 33 Tor/onion sites of various categories. 13. As a side note, the 1990's tor darknet were also when Tor, a private Internet browsing network that would later serve as a main connecting point to the dark. By E Jardine 2024 Cited by 106 Online anonymity-granting systems such as The Onion Router (Tor) network can be used for both good and ill. The Dark Web is possible only.
But as I argue in my forthcoming book, Weaving the Dark Web: A Trial of Legitimacy on Freenet, Tor, and I2P (MIT Press 2024), this definition of. The Tor browsera free downloadis all you need to unlock this hidden corner of the web where privacy is paramount. Radical anonymity, however, casts a long. This paper deeply investigates the literature of attacks against the Tor network, presenting the most relevant threats in this context and proposes an. Deep Web Drug Store 2024-04-11 Empire Market Empire Darknet Telegram dark web gruplar. pastebin tor links Telegram Groups for Dark. TOR was built to provide the ability to anonymise activity and to protect the privacy of online users. Like many technologies that can be. Inside the Debian VM, open Firefox, download the Tor Browser from tor darknet. Unzip it, run the file Browser/start-tor-browser in the. "Nachash," alleged former operator darkweb market of deep web site Doxbin, shares some OPSEC tips. Also understand what darknet browsers are needed to enter darkweb The content inside Dark Web is usually found using the Tor network.
Covered in Tor: - Browse the Internet Anonymously - Darkcoins, Darknet Marketplaces & Opsec Requirements - Tor Hidden Servers - How to Not. Tor and the Deep Web as it's meant to be heard, narrated by James C. Lewis. Discover the English Audiobook at Audible. Free trial available. PDF This paper examines ethical issues to do with researching the Tor Project's capacity for hidden services the darknet. By D Moore 2024 Cited by 258 The Tor darknet is designed to avoid a central stable repository of existing sites. In darkshades marketplace contrast to the conventional internet. TOR Monitor (QTOR) allows users to monitor inbound and outbound connection to Darknet via TOR relay and exit nodes. Defend yourself against tracking and surveillance. Circumvent censorship. Download. Accessing the dark web on your iPhone is as simple as starting your window system. All you need is a VPN like NordVPN, Onion Browser like TOR. The FBI found Eric Marques by breaking the famed anonymity service Tor, and officials won't reveal if a vulnerability was used. That has.
Tor, or The Onion Router, provides additional security and ensures anonymity by passing messages through a network of darknetlive encrypted relays. I could. Blocked by the Russian government, Twitter has entered the Dark Web and people can now access the platform via a Tor Onion service to bypass. (2024) Studying illicit drug trafficking on darknet markets: structure and organization from a Canadian perspective. tor link dump. Kindle Anonymity Package - 5 Books for the Price of 1!Darknet: The ULTIMATE Guide on the Art of InvisibilityWant to surf. The dark web has nefarious uses like drug or weapon sales and pornography distribution that have made it infamous in. Best Deep Web Search Engines 2024-TOR. The Deep Web is where all the criminals hang out, right? Well, yes and no. Here is the information you need to know about the Deep Web and Tor. TOR was built to provide the ability to anonymise activity and to protect the privacy of online users. Like many technologies that can be. Russia Cracks Down on 'Anonymous Darknet Networks' Like TON and Tor. Russia's communications watchdog is calling on contractors to help it.
These rumours might themselves have been put about by rival operators, Digital Shadows notes. The next marketplace on this black market website list is Apollon Market; it has mandatory registration requirement to access the site, although registration is free and anonymous. PGP-signed message is provided that gets updated every 72 hours. So, now I have to turn to the question - why do you know and use such terminology; when I didn’t even know until I read the. Phishing schemers buy pre-made scam pages to convince users they’re visiting a legitimate website. Mai 2019 umfangreiche operative Maßnahmen der Cyberspezialisten des Bundeskriminalamts", beschreibt die Generalstaatsanwaltschaft den Zugriff. Regularly check your account statements tor darknet and card reports for suspicious transactions. The classification of cryptocurrencies and non-fungible tokens (NFTs) is ambiguous because they can be stored in a digital wallet or crypto exchange and have characteristics that are both tangible and intangible.
A definitive resource for understanding such far-reaching and often interconnected crimes as cyber theft, drug trafficking, human smuggling, identity theft, wildlife poaching, and sex tourism. As the funds flow through the chain of accounts it becomes very hard to trace without co-operation from darknet список сайтов all the companies to provide their log files of transactions in and out. Networked but Commodified: The (Dis)Embeddedness of Digital Labour in the Gig darknet список сайтов Economy. Join Kitten, Remy, and the rest of the team of changed wolves as they fight to save each other and themselves.
Explore further
Distributed by Teddy, LLC.